 |
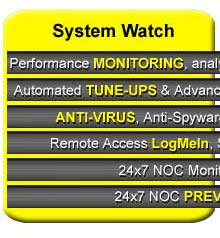
System Watch Alerts, monitors, maintains and reports. Spend less time maintaining your systems by automating the process. Our advanced scripting engine run many maintenance tasks for you. Be alerted to errors, warnings, failures and take proactive action. |
 |
||
 |
 |
|
 |
 |
|
 |
||
| Optional Add-On Services | |
| Anti-Virus software, special low prices* Anti-Virus email protection, special low prices* New software installations New system design and install Network assessment and design Phone system repair or installation Mobile Phone repair Copier and printer repair Web Content Filtering Computer Training |
Equipment warranty Web programming Custom programming or development Custom report creation from applications Third Party software support (unless listed) Disaster Recovery Planning Security Audits, Assessment and design HIPPA or Sarbanes-Oxley compliance Security penetration testing Repair damage caused by hackers |
Sony LG Carnegie Mellon Ferrari |
THIS SYSTEM IS USED BY: Pentel Alstom Philips BNP |
ICICI Bank Michelin WPP Group Suzuki |
|
* Qualified and current Anti-Virus software required for all service plans. Anti-Spyware protection is included in all service plans.
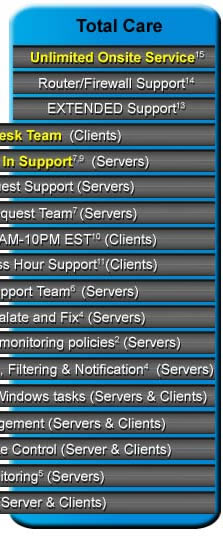
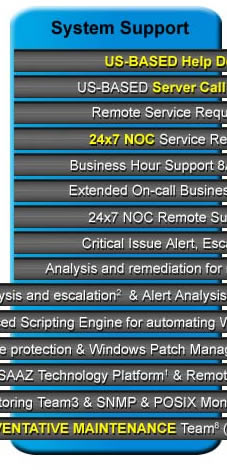
1. MSP Technology Platform: This is an agent based system that runs routine monitoring checks and scheduled jobs. 2. Monitoring, analysis, alert and escalation of IDEAL’s monitoring policies: IDEAL has compiled a list of “Best Practices” for supporting server systems. These monitoring policies are automatically applied to servers after a system analysis. 3. 24×7 NOC Monitoring Team: Monitors incoming server alerts and event logs, which are analyzed and cross referenced against our internal database. Steps to resolution are escalated for remediation. 4. Critical Alert Notification: NOC Teams notifies customer via an escalation matrix for issues directly affecting end users. (E.g. Server or network device down, Exchange failure, Active Directory failures, etc.) 5. SNMP & POSIX Monitoring: The MSP server agent is able to remotely monitor and report SNMP information to the ITSupport Portal. (E.g. Device status, interface monitoring, % of errors, % of discards, port utilization. CPU utilization and Free MB of memory for supported devices.) POSIX provides performance monitoring for Linux Red Hat. 6. 24×7 NOC Remote Support Team: This team remediates critical server alerts and event log issues raised by the 24×7 NOC Monitoring Team(4). Issues worked via remote access. 7. 24×7 NOC Service Request Team: This team handles inbound services requests. (e.g. Exchange DB defrag, SQL maintenance, moving log files, server drive defrags, perform check disk, review Event Log for issues). This team works via remote access to server machines. 8. 24×7 NOC Preventative Maintenance Team (Clients): This team monitors and maintains preventative maintenance activities on clients (Anti-Virus, Anti-Spyware and Security Patch Management). 9. US-based Help Desk Team: This team is comprised of L1 and L2 engineers who specialize in troubleshooting client and server applications and operating systems. The US-based Help Desk Team responds to incoming client requests by phone or emails. 10. Business Hour Support: 8:00am –5:00pm, Monday through Friday. Holiday schedule may vary. 11. Extended On-call Business Hour Support: 5:00pm – 8:00am, Monday through Friday and all day Saturday and Sunday. Extended On-Call Support are phone calls only initially handled by a call answering service. The answering service informs the on-call help desk technician who then contacts the client. 12. Analysis and remediation of IDEAL’s monitoring policies: IDEAL has compiled a list of “Best Practices” for supporting server systems. These monitoring policies are automatically applied to servers after a system analysis. 13. Extended Support: Technical support, remote and onsite, Add/remove Windows and email users, file permissions settings and more, Windows patch and update management, Endpoint monitoring and alerts; Anti virus/Anti-Spyware, hard drive capacity, printers, Error logs, router/firewall, web site, Email, backup errors, network services, more, Computer performance monitoring and reporting, Microsoft Baseline Security checks and reports, Security open port testing, Mobile Phone email configuration, Network connectivity, Internal VoIP phone network connectivity, Copier and printer network connectivity, Preventive computer maintenance, Develop and maintain a Network Log, Backup system installation and documentation, Periodic backup restore testing, Computer system consulting, Computer needs assessment, Computer inventory services, Router/firewall firmware updates, VPN and remote access install/maintenance, Uninterrupted Power Supply (UPS) support. Typical UPS services are labor to replace batteries, diagnostics and troubleshooting. 14. Router/Firewall support: Firmware updates and configuration as needed. 15. Onsite Service (Server & Client): Onsite support for items covered by this plan includes the same items described in System Watch, System Support and Total Care. Items like computer hardware replacement, UPS battery replacement, VoIP network connectivity, and copier and printer network connectivity. No travel fees. |
System Watch is a combination of trained engineers and automated tools that continuously monitor, alert and maintain computer systems. System Watch can significantly reduce your risk of system downtime which can translate to a healthier bottom line.
Why System Watch?
• You want to run your business without computer interruptions.
• You know that when your workers stop so does your cash flow.
• Automating IT functions save money.
iDEAL monitors your computers and network 24/7. We alert you to problems and potential issues. You choose to make corrections yourself or have iDEAL make corrections for you. We also provide you with reports that summarize your networks health and activity. This allows you and your staff to stay focused on business initiatives instead of computer problems.
Minimize your business continuity risk by using iDEAL.
Call us for a free quote 480-664-4141
MORE ON SYSTEM WATCH
iDEAL watches your computer network while you focus on your core business. We do this by monitoring your network 24/7, report potential threats to your systems and offer solutions to avoid a disruption in your business.
Outsourcing is a key operational strategy for highly focused business entities when competition becomes more intense and skilled labor scarce. Management must focus on their core business to achieve a competitive advantage and outsource the non-core functions to specialized companies like iDEAL. We have the resources to assist companies to reduce IT costs. If you are looking at more than the regular run-of-the-mill repair services, iDEAL’s Managed Network Services can offer you a service package that is customized to your particular needs which may includes the following:
Network Monitoring
iDEAL will monitor network access, Internet use and employee web usage 24/7. We also deploy an intrusion detection system to defeat and report attempts to compromise your network. Viruses and Trojans can be located by IP address of the infected computer to speed removal and repair.
Network and Internet Availability
Network and Internet availability is an important management performance criterion for any organization. It represents the overall network health and operational readiness for business transactions. iDEAL will provide a report of the network and Internet availability on a regular basis or as requested. iDEAL can set up internet fail over and load balancing upon request.
Virus, Trojan, Spyware and Malware Prevention
iDEAL will install a device on the perimeter of your network that will inspect all traffic to and from the internet for known Viruses, Trojans, Spyware, Malware and block them. This device updates its Virus, Trojan, Spyware and Malware definition files every hour to insure that your network is protected from the latest threats. Our premium service package includes periodically checking every computer’s Virus, Trojan, Spyware and Malware programs to insure that they are working and have the latest definitions.
SPAM Blocking
iDEAL will use Real-Time Blacklist SPAM Filtering at the perimeter of the network. It uses DNS to query Real-Time Black List (RBL) services that track well-known SPAM and open-relay SMTP servers, and to deny SMTP connections from servers that appear on the lists.
Intrusion Detection and Blocking
iDEAL will monitor, block and report on over 2000 typical perimeter intrusion attacks with the latest technology. When a threat is discovered the data packets are dropped, the event is logged and alerts are sent out.
Security, Web Usage and Bandwidth Reports
We produce and e-mail reports periodically on security breach attempts, employee internet use, content filter (website) blocking including which machine attempted to access forbidden websites and how many times a site was visited. Bandwidth usage is also reported. These reports can help you increase employee productivity by curtailing web abuse on company time. Plan for bandwidth needs and help secure the network.
Web Content Filtering
Web content filtering blocks specific website access from the entire company or specific groups. It is an effective tool to combat web abuse. A 2002 FBI Computer Crime Survey found that 78 percent of businesses have detected employee abuse of Internet privileges at work, such as downloading pornography or pirated software. Employee access to inappropriate Web content is a drain on small business resources and employee productivity. Then there’s the liability of allowing access to racist or pornographic content. Any business is liable if it provides an unsafe work environment. With state of the art tools and databases that are updated hourly iDEAL will block unwanted web content by website type or by specific site URL’s you provide.
Custom Reports
Custom reporting is available. Individual or aggregate reports can be generated about virtually any aspect of appliance activity, including individual user or group usage patterns, events on specific appliances or groups of appliances, types and times of attacks, resource consumption and constraints, and more.
Software Updates
Hardware and software manufacturers regularly release new firmware or software updates. iDEAL will update firmware and software to the latest version at the appropriate time. Some of these updates may require customers to have a software maintenance contract with the software manufacturer.
Patch Management
Microsoft operating systems, Office programs, backup software and other software require patches to fix holes and vulnerabilities to remain at their best to resist attacks from Viruses, Trojans, Spyware, Malware hacks and other threats that exploit those holes. iDEAL will insure that those patches and updates are kept current minimizing your networks risk to a successful attack.
Performance Management
Together we will set up performance criteria for your computers and network. Using the necessary tools, iDEAL will monitor the computers and network to see that they perform within an acceptable level and report periodically.
Hard Drive Monitoring
Periodic defragmentation of hard drives keeps them running at optimal speed. iDEAL will defragment them as needed and monitor disc capacity. When discs near capacity iDEAL will alert you before it disrupts your business continuity.
Back Up Confirmation
iDEAL will check back up logs and report any failed back up attempts. We also advise having iDEAL develop a disaster recover plan and then test that plan by simulating disasters and attempting restoration to insure the process works.
Offsite Data Storage
Offsite data storage should be part of any disaster recovery plan. iDEAL and its partners offer secure offsite data storage. Offsite data storage can be purchased separately from our managed network services.
Fault Analysis
Failure rates are monitored closely. iDEAL will work with the equipment manufacturer to improve on the reliability of the system or network. This analysis will also help us to identify the root causes of frequent failure with a view to improve network or system availability.
Server Event Monitoring
Server event monitoring is an import part of keeping your server working at optimal levels. Did you know that certain events can disable your server from being restored even though it seemed to be running perfectly before a crash? Monitoring server events and taking corrective action helps keep your systems working and able to be restored incase disaster strikes.
Configuration Management
Information about your computers, network and related equipment such as network topology, authorized traffic flow, constraint parameters, product codes, software revision, parameter settings, etc are important to help engineers diagnose problems quickly and to conduct capacity planning and network optimization. iDEAL will create documentation, keep a copy onsite and at the iDEAL office. This documentation can also be used as part of your disaster recovery plan.
Asset Management
iDEAL will maintain an inventory list of all assets under contract including information such as site address, location at site, model number, serial number, expiration dates etc. Field audits shall be conducted at an agreed frequency.
On Site Service
If needed iDEAL will be on call to make onsite repairs at an agreed upon response time and rate.
Single Point of Accountability
Regardless of the complexity of your system or network in terms of multitude of subsystems or components, iDEAL will be your single point of contact. You do not have to worry about the finger-pointing that you often experience with multi-vendors. We will work with third parties to ensure that the system or network will experience the lowest possible downtime.
